What Is Spoofing? Understand AIS Spoofing as a Deceptive Shipping Practice
In early 2023, reports of AIS spoofing in a region off the coast of Crimea began to circulate. These reports indicated the presence of deceptive signals portraying the letter Z, a symbol associated with pro-war sentiments utilised by Russia during the Russian-Ukraine conflict.
What is AIS?
AIS is a tracking system that helps find and identify ships by sharing information electronically with nearby ships, base stations, and satellites. It enhances maritime safety by giving:
- The ship’s name and type
- Its location
- Its speed and direction
- Its current status
This system is mainly used in shipping and navigation.
What is spoofing?
AIS spoofing is the manipulation of a ship’s Automatic Identification System (AIS) to disseminate false information regarding a vessel’s actual location. This practice can serve various purposes, such as making a political statement, evading sanctions, or for piracy.
It’s essential to note that not all instances of spoofing are illegal or problematic. However, when spoofing breaches established regulations, it’s a compliance violation that may lead to severe consequences for all involved parties.
Following the Russia-Ukraine conflict and the imposition of sanctions targeting Russia (which include pricing restrictions on Russian petroleum products like oil), there’s been a noticeable increase in AIS spoofing incidents and other illicit maritime activities.
In response to this growing concern, the U.S. Treasury Department’s Office of Foreign Asset Control (OFAC) issued preliminary guidance in 2022 related to a maritime services policy concerning the transportation of Russian oil by sea. This serves as a significant reminder that the stakes are high.
According to these guidelines, entities within the maritime industry are required to monitor and flag abnormal shipping practices and be vigilant about their business partners. With this in mind, in this article, you’ll learn how to identify illicit AIS spoofing by leveraging the advanced technology solutions provided by Pole Star Global. Ensure consistent compliance with regulations, and any newly imposed sanctions using our four typologies of AIS spoofing as a reference.
Topics covered in this article:
- Recognise the Challenge of AIS Spoofing Within the Maritime Industry
- What Is Spoofing? Define AIS Spoofing and Understand How Deceptive Tactics Have Evolved
- Automatic Identification Systems: Application and Functionality
- Identify the Motive Behind Intentional AIS Spoofing
- The Intentional Manipulation of AIS Signals to Hide Illicit Activity
- Hiding Illicit Activity: Who Should Be Concerned?
- Identify AIS Spoofing: The Four Typologies to Look Out For
- Take Action: Key Takeaways to Identify AIS Spoofing
- AIS Spoofing Glossary
Recognise the Challenge of AIS Spoofing Within the Maritime Industry
The challenge of AIS spoofing in the maritime industry persists as a longstanding issue with significant consequences for global security, trade, and environmental protection. While the practice of deceiving authorities through false identities or obscured vessel information dates back centuries, spoofing has evolved with technological advancements, making it increasingly complex and difficult to combat.
Below, we provide an expanded explanation of this challenge:
- Historical context: Deceptive shipping practices have deep historical roots. Mariners used natural flags and disguises as early as the 17th century. This historical precedent highlights the enduring ingenuity of those seeking to deceive.
- Technological advancements: In today’s era of advanced technology, the maritime industry has developed systems like AIS to enhance transparency, safety, and regulatory compliance. However, technological progress has also led to more sophisticated deceptive tactics that manipulate or disable these systems.
- Impact of geopolitical events: Recent geopolitical conflicts, such as the Russian-Ukrainian war and the subsequent sanctions on Russia, have triggered an uptick in deceptive maritime practices. These events have provided a geopolitical backdrop that incentivizes some entities to engage in illicit activities for sanctions evasion and smuggling.
- The consequences of detection: When vessels engaged in illicit activities are detected, the consequences are severe. Sanctions, cargo seizures, legal actions, and damage to the reputations of both the vessels and their owners can ensue. Consequently, these vessels may be rendered unusable for extended periods, leading to substantial financial losses for their operators.
Efforts to address AIS spoofing involve a combination of technological advancements, international cooperation, and enhanced enforcement to ensure the integrity of maritime operations and security.
What Is Spoofing? Define AIS Spoofing and Understand How Deceptive Tactics Have Evolved
AIS spoofing is an umbrella term used to describe the provision of false positional, navigational, and speed data so that the target vessel appears where it’s not. It’s a behaviour used for sanction evasion. Within this category, multiple tactics are used involving various identifiers, transmitters, and GNSS manipulation techniques. As our methods for recognizing AIS spoofing events advance, so do the deceptive tactics used.
AIS spoofing is a form of stream poisoning that takes advantage of the manual nature in which AIS updates are given. Stream poisoning describes the corruption or injection of fallacious information into a data lake to degrade its integrity.
AIS developments through the years
In the year 2000, the implementation of AIS became mandatory for vessels falling under the International Maritime Organization (IMO) Safety of Life at Sea (SOLAS) convention. AIS was selected as the sole identification system for the maritime industry.
AIS was initially developed as a safety measure to prevent maritime collisions. Since then, AIS has evolved to be a ship-tracking device. Yet, because AIS wasn’t originally designed for such purposes, it means these systems are susceptible to human error and intentional manipulation (spoofing).
AIS spoofing efforts have grown more sophisticated, with individuals devising intricate methods to conceal their illicit activities. This trend became especially pronounced after the 2012 sanctions on Iran, as barred Iranian tankers resorted to deceptive tactics to gain unauthorised entry to international ports.
In more recent times, sanctions on Russia have also heightened the prevalence and sophistication of AIS manipulation.
Have you ever encountered AIS spoofing?
On the 24th of August 2023, we conducted a webinar titled “Unveiling Dark Fleet Secrets: Investigating STS Transfers And AIS Spoofing.” During this webinar, we asked the audience: Have you ever encountered AIS spoofing? The results were as follows:
- 24% of respondents had experienced instances of AIS spoofing.
- 58% of respondents had not encountered AIS spoofing.
- 19% of respondents didn’t know what AIS spoofing was.
Focusing on this final result: How can key stakeholders in the maritime industry detect illicit activities like AIS spoofing if they lack awareness of what it entails or what to watch for?
At Pole Star Global, we’re working to address this knowledge gap, helping key stakeholders identify illicit shipping activities and remain compliant at all times.
If you too aren’t familiar with AIS spoofing, then utilising Pole Star Global’s advanced real-time data analytics, historical data comparison, and behavioural analysis capabilities will deliver unparalleled support in detecting anomalies and deviations in vessel behaviour.
At Pole Star, we don’t rely on algorithms, but flag potential spoofing incidents ourselves, analysing each instance on a case-by-case basis for accurate results. Later in this article, we will demonstrate how our software can be used to identify spoofing by outlining the four AIS spoofing typologies to look out for.
Automatic Identification Systems: Applications and Functionality
As previously discussed, automatic identification systems were originally introduced primarily for collision avoidance. This technology meant vessel captains could see the positions of other craft in their vicinity.
Today, AIS is mandated for ships exceeding 300 gross tonnage and for all passenger ships. With this mandate, the application of these systems has expanded to include:
- Traffic monitoring: Ensuring there’s sufficient space for ships in congested shipping lanes.
- Identifying smuggling operations: Tracking the movements of suspicious vessels engaged in smuggling activities.
- Search and rescue missions: Pinpointing the locations of ships in distress.
- Accident investigation: Assisting investigators in reconstructing the events leading up to collisions or sinking.
- Navigation aid: Providing critical information to plan safe routes through potential hazards.
Understand how automatic identification systems deliver results
AIS utilises satellites and radio waves to transmit encoded messages, which are subsequently received by other satellites and ground stations.
These encoded messages contain comprehensive information about the ship. This includes a vessel’s IMO number, name, type of ship/cargo, ship dimensions, destination, call sign, MMSI number, and other parameters. Each ship’s MMSI number is a unique nine-digit code.
To transmit information, ships employ specific radio channels (87B and 88B, which operate in the very high-frequency range).
Typically, these signals are limited to a range of approximately 20 miles because they follow a straight-line path and are unable to curve around the Earth. However, modern satellites have extended the transmission range considerably. Yet, doing so has introduced another challenge. That is, an excessive number of ships simultaneously broadcasting their location data would overwhelm the system. Therefore, ships must take sequential turns when transmitting informational data.
To globally organise shipping location data, Self-Organized Time Division Multiple Access (STDMA) links are employed. STDMA operates using one-minute frames that are divided into 2,250 time slots. Each vessel across the globe is allocated one or more of these slots to transmit its AIS message.
What’s important to note here is that every vessel must manually input its AIS message, which can lead to unintentional or intentional errors. AIS spoofing is the intentional alteration in this messaging.
Identify the motive behind intentional AIS spoofing
The motives behind deliberate AIS spoofing vary as we’ve detailed below.
Ship identity deception
Individuals can use AIS messages to disseminate information about fictitious vessels, including details about a ship’s identity, location, and cargo type.
For instance, fraudulent ship locations can be manipulated to make it appear that a given vessel is in the international waters of a hostile nation, provoking that nation to take defensive measures.
Alternatively, the actual location of a genuine ship can be falsified, creating the illusion that the vessel is simultaneously present in multiple locations, thereby concealing its true whereabouts.
For example, the HMS Defender gained notoriety on June 24th, 2021, when it navigated within 12 kilometres of the Crimean coastline, waters recognised as Russian territory. In response, the Russian Defense Ministry asserted that it had fired warning shots and dropped bombs as a deterrent, although Britain’s Ministry of Defense refuted these claims.
There’s reason to suspect the two parties engaged in a form of virtual naval diplomacy. This involves the strategic deployment of technology to influence or communicate with other naval or maritime entities, typically for political or strategic purposes, without requiring direct physical presence or confrontation. In this example, a live webcam feed showed the HMS Defender docked 300 kilometres away in Odesa, Ukraine.
Trickery with navigation aids
At times, counterfeit messages about navigational aids may be transmitted. This can compel a ship to alter its course. The motive behind such spoofing is to manipulate a ship’s route, coercing it into a specific location for potential hijacking.
Fake collision alerts
False information can be transmitted to create the appearance of two ships on the verge of a collision. Consequently, the ships alter their courses. Information can be manipulated to the extent that, upon changing course, one of the ships is directed towards an actual collision.
Search and rescue deception
Counterfeit distress signals are transmitted to create the illusion that a ship or its crew on board are in trouble. Other ships are duty-bound to provide assistance. This strategy is used to entice a ship into a trap.
Weather lies
AIS can be employed to exchange weather information among ships. Bogus weather reports can be transmitted through a ship, falsely indicating calm conditions when a storm is approaching. This deceptive information could potentially endanger a vessel.
AIS takeover
It’s even possible for someone to hijack AIS signals by transmitting a stronger signal simultaneously. Messages are frequently altered to create the appearance that the ship is transporting prohibited hazardous cargo.
Sanction evasion and other illicit shipping activity
Modifying a ship’s identification and location data to conceal its true origin and destination enables such vessels to participate in illicit trade activities without detection. The objective is to evade sanctions and undermine international efforts aimed at enforcing economic restrictions.
In this article, we concentrate on this form of AIS spoofing, as it is the most frequently employed. We will elaborate on the four distinct spoofing typologies typically used to evade sanctions, explaining how you can identify them using Pole Star Global‘s technological solutions.
The Intentional Manipulation of AIS Signals to Hide Illicit Activity
Disabling AIS systems offers a simpler method to conceal illicit shipping activities, yet it is readily detectable.
Going dark (or dark activity) is a term used to describe a situation where a ship deactivates its AIS system, making the vessel untraceable. This approach is simpler and easier than AIS spoofing, yet presents a substantial risk for wrongdoers. This is because it’s easily detectable by nearly every maritime domain awareness system available.
It’s important to note that attempting to identify dark activity without the appropriate technology can result in numerous false alarms, consuming valuable resources. To address this challenge, Pole Star Global identifies activities worthy of investigation, considering factors such as vessel and crew intent, domain expertise, and advanced maritime AI technology.
Creating more sophisticated deceptive tactics using AIS spoofing
Because dark activity is easy to spot, more sophisticated strategies have evolved to hide illicit activity. These emerging strategies aim to create a ‘business as usual’ illusion. That is, instead of working to conceal themselves and their unlawful actions, ships use AIS spoofing methods to blend in with regular maritime traffic. Below we’ve identified the main ways AIS signals are distorted.
- Dual transmission: Dual transmission utilises multiple AIS transmitters on a single vessel, each broadcasting distinct information linked to separate International Maritime Organization (IMO) numbers. This practice generates ambiguity regarding the vessel’s true location and its unique IMO number.
- Identity tampering: Identity tampering refers to the deliberate falsification of a vessel’s AIS broadcasted data. It also includes alterations to a ship’s physical attributes, all with the intention of misrepresenting its true identity. Note that identity tampering does not include tampering with a vessel’s registered identity, otherwise known as IMO number fraud.
- Identify theft: Identity theft occurs when one vessel assumes the identity of another operational vessel, resulting in the duplication of the same transmitted identifiers. This makes it difficult to tell the two vessels apart and know the true location of the ship in question.
- Identify laundering: Vessel identity laundering is similar to identity tampering. A dirty vessel assumes the identity of a clean vessel. Yet, the key difference between identity tampering and identity laundering is the falsification of the ship’s IMO number in the latter. Identity laundering typically involves the following elements:
- Deliberate alterations or misrepresentations of a vessel’s physical, digital, and registered identities.
- The adoption of a “shell” identity which is an IMO-registered identity obtained through deceptive means, is commonly known as IMO number fraud. A shell identity has no authentic connection to any specific ship.
- Location tampering: Location tampering employs machine-generated location data or paths to conceal the vessel’s actual location.
- AIS handshake: A decoy vessel is used as a disguise. The “dirty” vessel assumes the identity of the “clean” vessel while sailing in close proximity, allowing the latter to continue its journey undetected in the dark. Upon return, the vessels recreate the switch, leaving the “clean” vessel unscathed.
- MMSI manipulation: Ships can tamper with the MMSI numbers programmed into their AIS systems. There are three main ways MMSI numbers are manipulated:
- The same MMSI number is used for many different ships meaning these ships cannot be distinguished from one another. So, instead of seeing separate ships on the map, it looks like there’s only one ship that’s teleporting across the ocean at impossible speeds.
- The use of random or nonsensical sequences.
- The first three numbers are added to indicate the country of origin, but these numbers are then followed by all zeros.
Any form of AIS spoofing will leave a distinctive footprint such that occurrences can be predicted. The team here at Pole Star specialises in identifying these distinctive patterns to predict spoofing, and later in this article, we share our insights. We identify the four typologies of AIS spoofing used to hide illicit activity and present the key characteristics of each.
Hiding Illicit Activity: Who Should Be Concerned?
AIS spoofing implications for commodity traders
Businesses operating within the EU, G7, and Australia must refrain from purchasing Russian crude oil that exceeds the defined price limit. They should also avoid chartering and accepting cargo from vessels under Russian jurisdiction, including those flying the Russian flag or owned by Russian entities. It is crucial to remain vigilant and detect any attempts to conceal these affiliations through flag and company alterations. With the use of Pole Star Global’s PurpleTRAC solution, commodity traders will receive real-time updates on these activities as they happen.
AIS spoofing implications for financing banks
Financial institutions with expertise in the relevant regulations, especially within the aforementioned jurisdictions, should exercise prudence. Banks handling transactions in US dollars and euros should refrain from engaging in financial dealings with vessels under Russian control, particularly those operated by SDNs (Specially Designated Nationals). Additionally, they should avoid any transactions that could potentially violate the specified price limit. It is advisable to utilise technology for comprehensive transaction analysis to promptly detect and address compliance concerns.
AIS spoofing implications for insurers and operators
Similar principles apply to insurers and operators. They should conduct thorough checks on vessels, both before insuring them and while working with P&I clubs (Protection and Indemnity clubs).
AIS spoofing implications for port operators
Port operators bear the responsibility for vessel screenings, with no other entities currently conducting these verifications, especially within the EU. Therefore, it is imperative that EU port operators take proactive measures to ensure compliance.
AIS spoofing implications for Russian entities
Blocking Russian entities that are subject to sanctions is vital. However, alongside imposing sanctions, it’s equally important to bolster compliant entities by rigorously conducting Know Your Customer (KYC) procedures.
AIS spoofing implications for businesses in the maritime sector
Companies offering services to ships or involved in maintenance should make due diligence a top priority. This involves implementing robust tools and procedures to ensure adherence to applicable regulations and sanctions.
Identify AIS Spoofing: The Four Typologies to Look Out For
AIS spoofing presents a complex challenge for detection, as threat actors employ various methods to falsify and manipulate their positional, navigational, and speed information. At Pole Star Global, our commitment is to empower your organisation with the knowledge and resources needed to effectively identify AIS spoofing in real-time, ensuring compliance.
To that end, we’ve identified four different typologies of AIS spoofing. We will explain each of them, providing characteristics of the AIS signal trails to watch for.
Spoofed signals can vary widely, with the underlying data ranging from basic attempts that are easily identified to more sophisticated ones that create realistic-looking data. However, each spoofing method will have a distinct signature, enabling the team here at Pole Star to predict AIS spoofing in action. In this next section, we share our insights into how we achieve this.
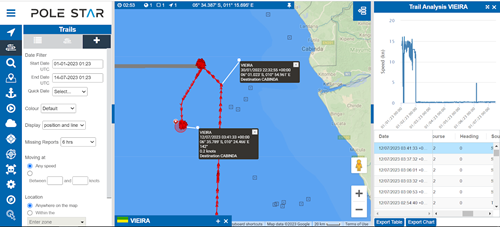
AIS spoofing typology #1: Long-term anchor spoofing

As the name suggests, for long-term anchor AIS spoofing, a vessel provides false data over an extended period, depicting itself to be in one location for this time, even when it’s not.
For example, consider the ship named Vieira. This vessel has been falsifying its location since January 2023, making it appear as if it is situated just off the coast of Angola. As of the time of this writing, the vessel continues to engage in AIS spoofing.
However, information from human sources and imagery indicates that this data is inaccurate, and the vessel is, in fact, operating out of Venezuelan ports.
Apart from the linear nature of the ship’s movements, Vieira’s AIS data exhibited inconsistencies compared to normal data and typical ship movement patterns.
Viera gives the appearance of being at anchor, indicating the ship may be used for offshore storage. However, a thorough analysis of the vessel’s signal activity, along with human or imagery sources, confirms the ship’s “transmitted” location is inaccurate.
Vessels seeking to evade Venezuelan sanctions frequently employ long-term anchor spoofing as a tactic. These vessels falsify their locations, claiming to be off the West Coast of Africa (“WCoA”). The goal is to conceal their visits to Venezuelan ports for extended periods.
AIS spoofing typology #2: Circle spoofing
Circle spoofing is commonly employed in regions where vessels load cargo.

Circle spoofing is commonly employed in regions where vessels load cargo.
As depicted in the image, the circle spoofing tactics form a geometric circle, and smart spoofers will begin and end this spoofing while their vessel is within the circle
For example, the ship YU I made three visits to the Persian Gulf, and each time the ship arrived at the Basra terminal. During each visit, the YU I engaged in spoofing for a period ranging from one to five days before departing. It is suspected that during these voyages, the YU I spoofed its location to facilitate the loading of Iranian gas.
As depicted in the image, circle spoofing creates a geometric circle, consistently starting from the northernmost area. The spoofing techniques illustrated in this example demonstrate a high level of sophistication, as the ship’s captain aimed to initiate and conclude the spoofing while the vessel remained within this circular pattern.
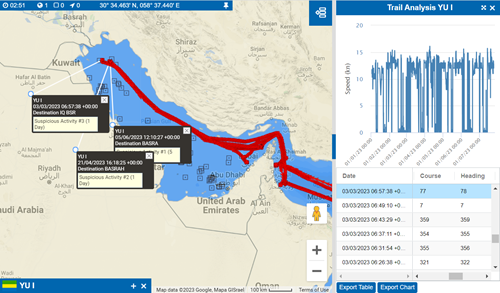
Fig. 1.2: The Yu I made three visits to the Northern Persian Gulf in March, April, and June of 2023. During these voyages, the Yu I spoofed its location for what we suspect was to load Iranian gas.
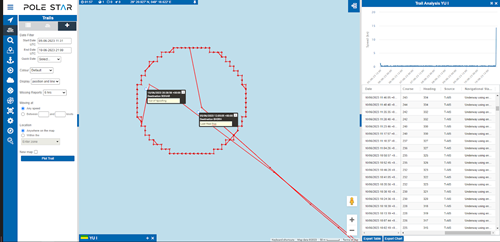
Fig. 1.3: The Yu I’s spoofing was in a geometric circle. Furthermore, its behaviour showed a level of sophistication as the ship’s captain aimed to begin and end its spoofing while the vessel was within this circle.
AIS spoofing typology #3: Slow roll
During slow roll AIS spoofing, a vessel mimics movement, but at suspiciously sluggish speeds, with no economic rationale.
During such spoofing events, you may also notice the vessel moves in ways that are inconsistent with nautical charts, or contrary to ordinary traffic. Sometimes we see bad command and control, such as when a time delay between when an AIS transponder is turned off, and when the same transponder is turned back on.

In the example below, you can see that the HMS Legend initiates its suspected spoofing activity slightly north of the Bosphorus. The vessel consistently transmits AIS positions at exceptionally slow speeds, which sharply contrasts with the typical faster traffic flow in the area.
There has been a notable increase in slow roll spoofing incidents in the Black Sea region, including areas near Tuapse, Russia.
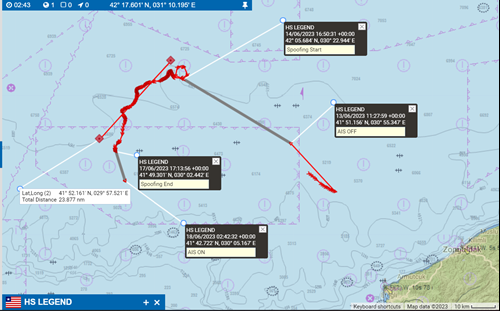
Fig. 1.4: The HS Legend engaged in suspected spoofing between 13 – 18 June 2023. The vessel moved at extremely slow speeds during this period, and our analysis of its signals suggests that the data is not genuine.
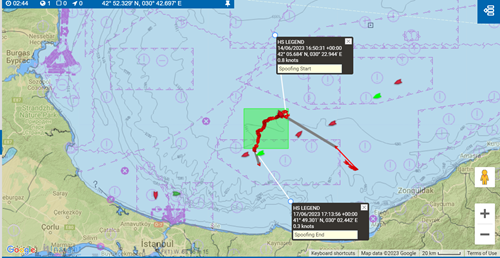
Fig. 1.5: The HS Legend’s movement during this period was not consistent with traffic from all other vessels operating in the area at this time, and served no economic purpose.
AIS spoofing typology #4: Pre-programmed route
The methods for detecting AIS spoofing are becoming more sophisticated and accurate. This is creating an arms race, where spoofing tactics are evolving from amateur to more sophisticated methods in reaction.
Today, the most convincing form of spoofing occurs when a vessel is meticulously programmed to follow plausible routes. This involves either replicating or obtaining historical AIS data to accurately simulate the vessel’s course or engaging in thoughtful planning to create the impression of a legitimate economic voyage.

For instance, in the example shown below, we illustrate the voyage of the ship named Onrense, which we suspect is engaged in AIS spoofing.
Upon initial inspection, the ship’s route appears genuine. However, based on additional information we’ve gathered, it’s likely that Onrense is following a pre-programmed route.
How did we arrive at this conclusion?
We considered the ship’s history. We know that Onrense engaged in long-term spoofing off the West Coast of America between April and July 2023. Additionally, the vessel also employed circle spoofing off the coast of Trinidad and Tobago for two weeks in July. Based on this information, while the outbound leg does appear genuine, we suspect that this vessel is spoofing its location based on the available information.
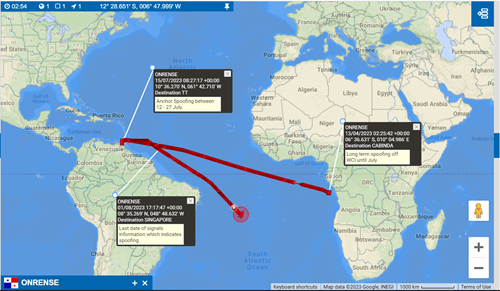
Fig. 1.6: The Onrense engaged in anchor or long-term spoofing off the WCoA between April – July 2023, and more briefly circle spoofing off the coast of Trinidad and Tobago for two weeks in July. While its outbound leg looks genuine, we suspect this is also spoofing based on information available to us.
Take Action: Key Takeaways to Identify AIS Spoofing
Using the four typologies of AIS spoofing mentioned above, we give you key takeaways to help you identify AIS spoofing using Pole Star Global’s PurpleTRAC and MDA solutions.
Action item #1: Identify unexplained activity off the west coast of Africa
Tankers may report their location as being just off the west coast of Africa, in places like Angola or Togo, while loading and transporting Venezuelan crude oil. Prolonged or unexplained lingering in this area, including reports that the vessel is at anchor, could be a sign that the ship is engaged in spoofing.
Action item #2: Watch for prolonged slow movement in the Black Sea
Tankers loading cargo at Novorossiysk or Tuapse in the Black Sea may report movements at extremely slow speeds, often less than 1 knot for at least two days. These movements may also deviate from the normal traffic patterns in the area.
Action item #3: Understand movements that have no economic purpose
Spoofing vessels may generate AIS tracks that lack a clear economic purpose. For example, vessels might approach a port and then abruptly change direction. It’s worth noting that instances of spoofing, ship-to-ship transfers, and AIS disablement have been observed around Basra and Iraqi port anchorages.
Action item #4: Look for geometric or recurring patterns
Be vigilant for geometric or recurring patterns of movement. Spoofing can manifest itself in various ways, such as vessels following perfect circular routes, moving in random but alternating patterns over set distances, or repeatedly following the same track files.
Recognising these patterns can help you identify spoofing activities.
AIS Spoofing Glossary
- AIS Spoofing: AIS spoofing is the intentional alteration or fabrication of Automatic Identification System (AIS) data by ships or other entities to mislead or deceive a vessel’s identity, location, or other information.
- GNSS: GNSS (Global Navigation Satellite System) is a satellite-based navigation system that provides accurate positioning, navigation, and timing information to users worldwide.
- AIS: AIS (Automatic Identification System) is a maritime communication system that allows ships and vessels to transmit and receive essential information such as identity, location, course, and speed to enhance navigational safety and awareness.
- IMO: The International Maritime Organization is a specialised agency of the United Nations responsible for regulating and coordinating international shipping and maritime activities to ensure safety, security, environmental protection, and efficiency.
- MMSI number: Maritime Mobile Service Identity (MMSI) is a unique nine-digit number assigned to AIS communication devices, used for identification and communication purposes in the maritime industry.
- IMO number: The IMO number, also known as the International Maritime Organization number, is a unique seven-digit identifier assigned to individual ships and vessels to facilitate their global tracking and identification. Unlike MMSI numbers, a ship will only ever have one IMO number throughout its operational life.
- Self-Organized Time Division Multiple Access (STDMA): Self-Organized Time Division Multiple Access (STDMA) is a maritime communication protocol that efficiently manages and allocates time slots for data transmissions in a decentralised manner, enhancing the reliability and coordination of vessel communication in congested maritime areas.
- Dark activity: Turning off a ship’s AIS to deliberately create a transmission gap with the intention of concealing operations.
- Dark fleet: A group of vessels primarily used for transporting sanctioned or illicit goods, such as oil and petroleum products, while attempting to evade detection or regulatory oversight.
- Maritime Domain Awareness (MDA) system: A Maritime Domain Awareness (MDA) system is a comprehensive and integrated surveillance and information-sharing platform used by coastal authorities and maritime agencies to monitor, track, and analyse vessel traffic and activities within a specific maritime region or domain.
- Dirty vessel: A dirty vessel refers to a ship that doesn’t comply with specific regulations and sanctions.
- Clean vessel: A clean vessel refers to a ship that has no history of any wrongdoing.
- Dual transmission: Dual transmission utilises multiple AIS transmitters on a single vessel, each broadcasting distinct information linked to separate International Maritime Organization (IMO) numbers. This practice generates ambiguity regarding the vessel’s true location and its unique IMO number.
- Identity tampering: Identity tampering refers to the deliberate falsification of a vessel’s AIS broadcasted data. It also includes alterations to a ship’s physical attributes, all with the intention of misrepresenting its true identity. Note that identity tampering does not include tampering with a vessel’s registered identity, otherwise known as IMO number fraud.
- Identify theft: Identity theft occurs when one vessel assumes the identity of another operational vessel, resulting in the duplication of the same transmitted identifiers. This makes it difficult to tell the two vessels apart and know the true location of the ship in question.
- Identify laundering: The deliberate alteration or misrepresentation of a vessel’s physical, and digital identities, as well as falsifying a ship’s IMO number. There are two types of identity laundering:
- Type one: This is a direct laundering operation whereby a dirty vessel directly assumes a shell identity.
- Type two: This is an indirect laundering operation where a “clean” vessel assumes the shell identity and the first vessel assumes the clean vessel’s now-vacant identity.
- Identify change: An alteration to the vessel’s maritime mobile service identity (MMSI), often accompanied by modifications to other identifying information, such as the name and call sign.
- Location tampering: The intentional manipulation of a vessel’s AIS broadcasted information and/or physical attributes in order to deceitfully change its identity (source: C4ADS, 2021, “Unmasked – Vessel Identity Laundering”)
- Identity theft: When one vessel adopts the identity of another vessel currently in operation, resulting in a duplication of the transmitted identifiers.
- AIS handshake: Employing a decoy vessel as a camouflage technique, where the “compromised” vessel assumes the identity of a “clean” vessel, sailing in close proximity, while the authentic “clean” vessel operates discreetly towards its destination. Upon completion of its mission, the vessels reverse the switch, allowing the unaffected “clean” vessel to resume its original identity.
- MMSI manipulation:
- Shell company or vessel: A business entity or vessel established primarily to conceal the true ownership of vessels or cargo, facilitating illicit activities and evading sanctions.
- Long-term anchor spoofing: A vessel gives the appearance of being at anchor for an extended time period to its actual location.
- Circle spoofing: A technique often used in shipping ports. Spoofed signals create a perfect circle.
- Slow roll spoofing: A vessel simulates movement in a general direction (although not always in a straight line) at unusually slow speeds that lack an economic purpose.
- Pre-programmed routes: A more sophisticated method for hiding a ship’s activity. Spoofed signals give the impression of a legitimate economic voyage using historical AIS data to simulate a vessel’s course.
- Flag hopping: Continuously altering the transmitted Maritime Mobile Service Identities (MMSIs), including flags, in order to evade detection, a practice that can also be employed for legitimate financial purposes, rendering it challenging to categorise as illicit activity.
- Ghost ships: Utilising the identity of a decommissioned or scrapped vessel to carry out unlawful activities without facing legal consequences.
- Threat actors: Individuals, groups, or entities that pose a risk or threat to the safety, security, or integrity of maritime operations.
- Sanctions targets: Specific vessels, companies, individuals, or entities that are subject to sanctions imposed by governments or international bodies, often due to violations of trade restrictions, international law, or security concerns.
- Shadow economy: Refers to the underground economy – the transaction of goods and services not reported to the government. Such transactions are conducted through smuggling, illegal trading, or other operations that are conducted outside the boundaries of official regulations and oversight.
- OFAC: The Office of Foreign Assets Control (OFAC) is a U.S. government agency responsible for enforcing economic sanctions and trade embargoes, regulating financial transactions involving sanctioned entities, and ensuring compliance with sanctions programs in the context of maritime trade.
- Ship owners: Individuals or entities who possess legal ownership and control over a vessel, including responsibility for its operation, maintenance, and commercial activities.
- Flag registries: Official authorities or organisations responsible for registering and regulating vessels under a specific flag or nationality, which determines the vessel’s legal and regulatory framework.
- AIS spoofing: The deceptive practice of transmitting false information or signals, often involving the manipulation of Automatic Identification System (AIS) data, to misrepresent a vessel’s identity, location, or intentions.
- Covered persons: Entities such as commodities traders, financial institutions, flag registries, ship charterers, and other relevant parties subject to compliance obligations under sanctions regulations and related measures.
- Price cap: A specified limit or maximum price that applies to certain transactions involving commodities like oil, often imposed as part of sanctions or trade regulations.
- Allied countries: Nations that have established friendly and cooperative relationships, often involving trade agreements and shared economic interests, which can impact maritime trade and activities.
- Shell companies: Entities that exist on paper but often lack substantial operations or assets, and they are sometimes used for various purposes, including potentially illicit activities such as sanctions evasion or concealing ownership.
- AIS transponder: A device used on vessels to transmit and receive Automatic Identification System (AIS) signals, which provide real-time information about a ship’s identity, position, course, and speed to enhance navigation safety and awareness.
- AIS data: Information transmitted by Automatic Identification System (AIS) transponders on vessels, including details such as a ship’s identity, position, course, and speed, used for navigation and tracking purposes.
- FCC community: The Federal Communications Commission (FCC) and its regulatory role in managing maritime communication systems and frequencies within the United States.
- T-AIS: The network of coastal-based AIS receiving stations and equipment on land used to track and monitor vessels’ positions and data within a certain range of the coastline.
- S-AIS: Satellite-Automatic Identification System is an advanced maritime tracking system that utilises satellite communication to provide global coverage of vessel positions and data, enhancing maritime safety and security.